The Internet of Things (IoT) encompasses a wide range and variety of items and equipment that are connected to the Internet via wired or wireless connections. These technologies are widely used for a variety of reasons, including communication, transportation, education, and commercial growth, and their popularity has risen fast.
However, as IoT becomes more widely adopted, privacy concerns about losing control over how our data is gathered and shared with others are becoming more prevalent. Any IoT ecosystem must adhere to strict privacy standards, and this is a key problem that prevents its wider acceptance. It is the ability to manage personal raw data that is immediately transmitted from sensors to the outside world that is causing
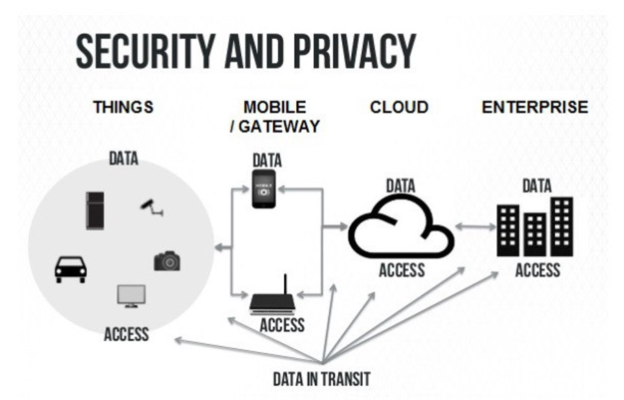 the most user dissatisfaction.
the most user dissatisfaction.
Source: https://miro.medium.com/max/1200/0*87qbJbXFN0OMhVpK.
1. Different security and privacy issues
Intelligent Things (IoT) give users a high degree of automation and control over how they do common tasks. Information is shared among a wide range of nonstandard computer devices. Microcontrollers, sensors, and actuator units may broadcast data and share it in order to facilitate better interactions. In addition, they can help humans to make decisions based on shared data.
Data is collected and sent between consumer devices or industrial machines through embedded devices. Physical changes can also be made by IoT devices. Those devices can be controlled either in close areas or remote areas over the Internet. As examples, we use linked consumer products such as smart appliances to illustrate the privacy problems highlighted in this article.
One of the reasons that make IoT devices vulnerable to attacks is that customers’ smart gadgets are being produced at a far faster rate than privacy-protection measures can be created.
Neglecting to change passwords and not updating devices have raised cybersecurity threats and the ability for dangerous apps to access sensitive data from IoT systems. Data breaches and other risks are more likely to occur as a result of such ineffective policies. Due to poor security procedures and regulations, IoT is considered a susceptible area for cyber attacks. In spite of the fact that a number of security measures have been created to safeguard IoT devices from cyber assaults, security standards have not been formally defined.
Privacy implies that information about individuals must be protected and may not be exposed without explicit consent under any circumstances. Every individual has the right to determine with whom to share their data
Traditional Internet users are affected by Internet privacy problems. However, in the IoT world, even people who aren’t using IoT services but are present in their surroundings may be affected by privacy problems. For example, the patient should be the only one to decide whether to share his heart conditions with the insurance company or not.
Due to the lack of clearly defined control domain boundaries in IoT settings, it is far more difficult to properly detect privacy infractions. People’s personal information must be protected, and acquired data must be utilized solely for the intended purpose. Last but not least, acquired data must only be retained for as long as it is absolutely necessary to have them.
2. Solutions for Privacy Access/Security Threats in IoT
The followings are some proposed solutions to overcome those security issues:
Authentication and Authorization
Due to the constraints of IoT devices, authentication in IoT settings might be difficult. For these constraints to be addressed, several researchers have developed lightweight alternatives. They use XOR operations to encrypt the data. Base on that, they implement a lightweight cryptography protocol. As a result, a standard RFID system for IoT applications may be configured to use this protocol’s hardware implementation.
Edge Computing and Plug-In Architectures
In the last few years, edge computing has become increasingly popular. In edge computing, data processing and storage take place in part at the device, rather than being sent and processed in the cloud. To address issues about latency, device limits, security, and most crucially privacy of users, Edge Computing makes more sense as data is being generated at the network’s edge.
Data Anonymization
Anonymous data are obtained by removing identifiable information that could be used to identify a person or object. Anonymous data is typically used to preserve user privacy. Anonymization, blurring, and denaturing methods have been tried in IoT applications, particularly with pictures and videos.
Digital Forgetting and Data Summarization
When using digital forgetting, we try to delete all the copies of a dataset. Data summarization on the other hand tries to hide the details of the data. By applying those techniques, we could make our users feel more comfortable and safe when they share their data because they know that the collected data will be deleted after serving the intended purposes.
3. Final thoughts
For even the most experienced developer teams, securing devices in an IoT network can bring new obstacles and difficulties. A breach might have huge consequences due to the inherent vulnerability of IoT devices. An IoT system that is mission-critical may be effectively protected by a thorough strategy and the proper tools.
4. References
https://www.mdpi.com/2076-3417/10/12/4102/pdf
https://www.hindawi.com/journals/wcmc/2018/1032761/
https://www.firstpoint-mg.com/blog/top-19-iot-security-solutions/
