Internet of Things (IoT) technology has brought many advantages to our life. At the prestigious annual conference in the GIoTS scientific community, many IoT topics were announced such as impacts, benefits, etc. Among them, there are Identity management and object recognition, which are IoT enabling Technologies. This technology provides an effective solution to the security problem, where IoT devices possess a large number of valuable resources and data. Today, let’s discover these things with Speranza.
I. What is Identity management?
In a tech that everything is interconnected, identity management is no longer centered around people. Devices can exchange data and automatically execute work, so the identity of each must be guaranteed. Identity management in IoT is a method of managing unique identifiers for each device in the system. This technology also ensures the communication and reciprocity of data between entities, preventing the possibility of intrusion to steal data. In addition, users still have the role of controlling and receiving information from devices, so they also need to be authenticated and authorized to access data.
 All things in IoT must be identity-managed, including users. Source: https://identitymanagementinstitute.org/identity-of-things-challenges-in-iot-identity-management/
All things in IoT must be identity-managed, including users. Source: https://identitymanagementinstitute.org/identity-of-things-challenges-in-iot-identity-management/
The identity management model on the Internet of Things is absolutely new, existing models cannot be applied because of the distinctive characteristics of IoT. It is the difference in the technology of interoperability between devices, the mobility of objects, and the endless scalability of the system. Solutions to the above problem are still being researched and developed every day, one of which can be identified by blockchain technology. This system allows peer-to-peer verification without the need of an organization, i.e. devices can authenticate themselves to each other. This network is divided into authenticated and observable nodes, which helps prevent third-party attacks.
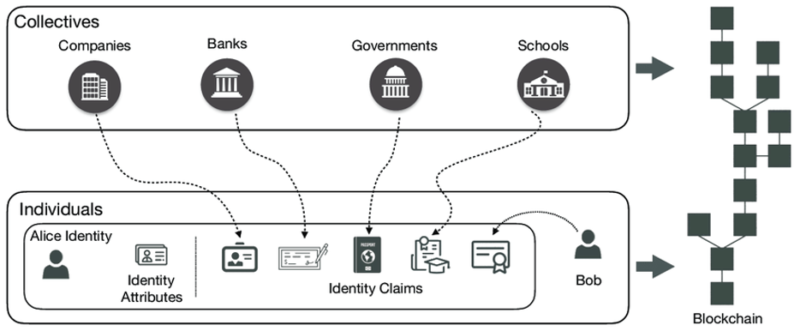
An Identity Management solution using blockchain can be applied to IoT. Source: https://www.mdpi.com/1424-8220/18/12/4215/htm
No model is totally secure, and Identity Management in IoT too. There are quite a few challenges for it such as password risks, the ability to access the system when information is leaked from users. From there, hackers can take control of IoT things. There is also the possibility of eavesdropping since most devices are linked to virtual assistants like Google assistant, which can then fake the identity of any entity in the system. However, Identity management technology is expected to be a new step to help the Internet of Things develop more and more. The higher the security, the larger the system can be built, such as a “universe” of smart devices.
II. Object recognition and the benefits in IoT
Object recognition is the ability to recognize and classify objects from images collected, for example through a camera. This is a technology-based on deep learning, toward artificial intelligence, one of the most high-level technologies today. Deep learning takes the data collected from the model, pushes it through algorithms in Convolutional Neural Networks (CNN), and then makes predictions. The more data collected, the higher the accuracy. In IoT, sensors are responsible for collecting data and processing it in real-time.
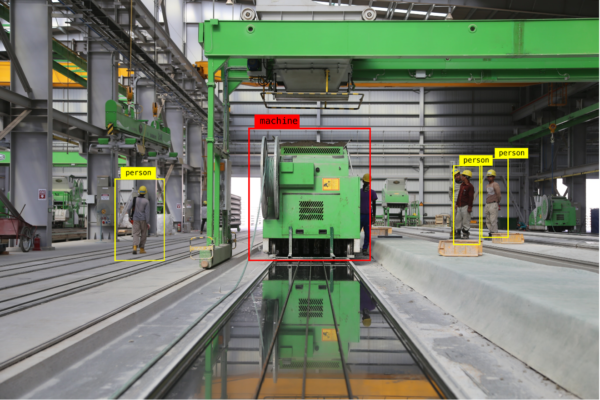
Recognize objects in the factory. Source: https://alwaysai.co/blog/using-object-detection
Object recognition is an advanced technology and is being utilized by IoT systems more and more. Here are some examples of its benefits.
– The core of the smart city.
Object detection helps regulate public transport, or use it to detect polluted areas and alert authorities. In addition, crime can be prevented by security cameras in smart surveillance systems. Suspicious actions will be reported to the system, helping to detect acts such as stealing, terrorism, etc.
– Improve manufacturing productivity.
Count, sort, and control products with real-time images. In addition, the IoT system with built-in object classification can also predict the status of machines for maintenance. Factory automation is also more precise. Some specialized production facilities such as oil or chemical can be used to detect incidents such as oil spills and gas leaks.
– In agriculture.
Image recognition helps the system detect diseases or sick plants, thereby treating pathogens or automatically watering. In addition, it can be used to spy on resources in the ground, or classify soil suitable for crops, automatically cultivate, etc.
III. Usage of Identity management and object recognition.
Obviously, Identity management and object recognition bring a lot of value. Integrating the above technology for the IoT system is essential, but it is not possible to do it. You need to follow the following steps before doing that.
1. Set up a space for the device and give it a name for identification. Also, create a scalable identity lifecycle that applies to all devices.
2. Establish strict security measures. The new device registration process should be based on these measures.
3. Secure access to IoT devices from users. Authentication or authorization procedures are enhanced to avoid intrusion into the system. It also protects personally identifiable information (PII).
4. Control the connection to the network of IoT devices and external organizations to the devices in their system.
5. Create a transparent authentication and authorization process for all entities in the IoT system.
Conclusion
Through the above article, we hope you have a better understanding of Identity management and object recognition in IoT. The above technologies will help more in everyday life. But for now, it’s just the beginning, we’ll get more and more advanced in the development of smart devices and technologies. To integrate Identity management and object recognition for your IoT products, look no further than contacting an expert like Speranza Inc. Contact us whenever you want IoT solutions for your business.
Reference Source
- https://www.iotforall.com/identity-management-iot
- https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3168605
